Tutorial: Secure Azure Functions with Azure App Registration
Overview & Implementation of Securing Azure functions using App Registration
In this blog post, I provide a step by step walkthrough to secure Azure function using App Registration.
I don't need to emphasize on the need to secure Azure functions especially those with Http triggers.
No one wants an Azure function in production to be accessible just from anywhere over the web.
We must ensure that only authorized entities can invoke or access them.
By default, there is some token called access keys that are generated for the functions which can either be supplied as a query string parameter or a header parameter (x-functions-key) just like you see below:
This is not enough security. “While access keys provide some mitigation against unwanted access, you should consider other options to secure HTTP endpoints in production. For example, it's not a good practice to distribute shared secrets in a public app” - Microsoft.
We need to fix this.
One way is to use AAD Authentication - Azure App Registration.
Azure App Registration - This one involves creating an application in Azure AD and configuring its permissions. This one needs to access creds (client secrets, etc) in code (better from an Azure Key Vault). It can be used to manage access to Azure resources through OAuth 2.0 and OpenID Connect protocols.
Depending on your specific use case and security requirements, you can select the method that best suits your needs.
If you need to access outside Azure environment, e.g Postman, client apps, use the App registration option.
Secure Azure function using Azure App Registration.
From Azure portal, navigate to the Azure function app
Navigate to Settings > Authentication
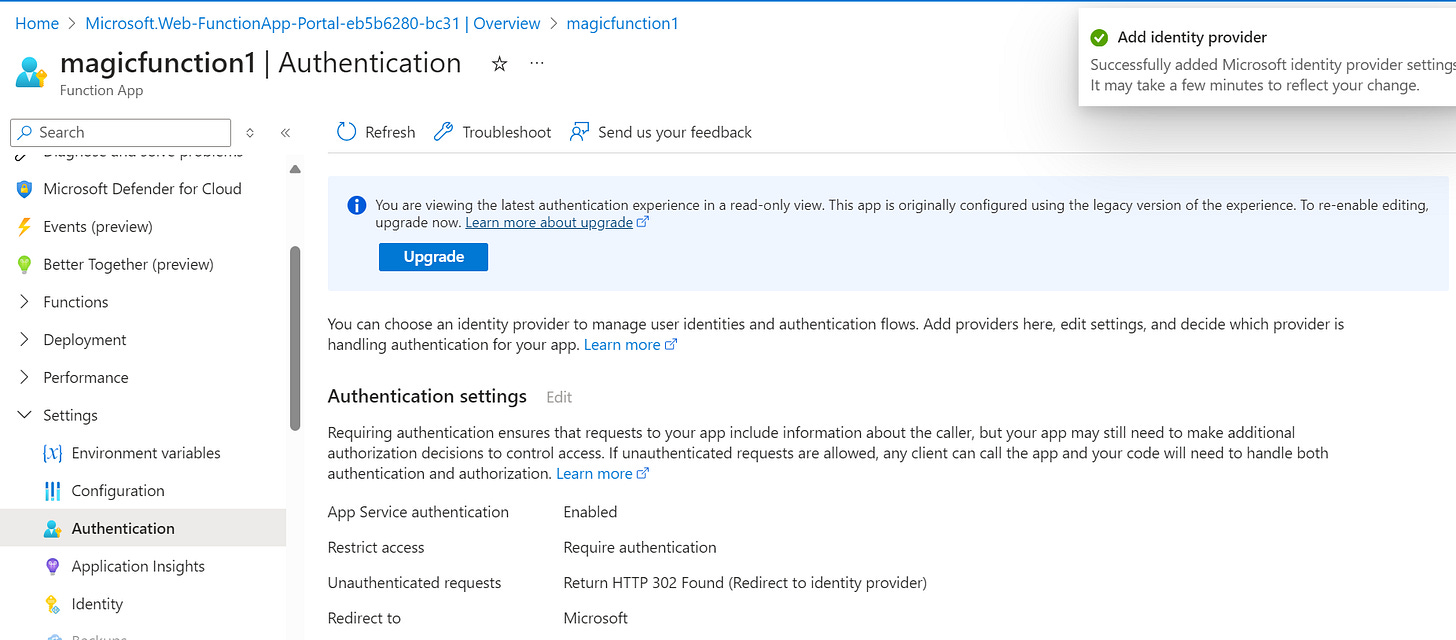
3. Click on Add identity provider and fill as shown below:
4. In the App registration type, you can choose to create a new app registration right from here or select an existing one which in this case I will use because I already have one created. See here on how to create an app registration
I am leaving everything else as they are:
Click on “Add” and you will be taken to this page showing you what you have configured:
Now let’s try to access the same azure function URL in the browser:
Now, you will be required to sign in with a valid credential to be able to send any request to it.
If you need to access this function from a postman or any rest client, you would just need to supply the OAuth credentials (tenantid, clientid, client secret) obtained from the App registration and you will be able to connect.
That’s it for today.