Behind The Scenes of Managed Identities
Secure Azure App Service with Managed Identity and Accept Authenticated Requests from External Clients via Azure AD
Happy new ‘AI Agentic’ year guys. I have a few contents around agents to share this year but before then, one more post about Managed Identities.
If you have a custom app hosted in App service that is currently being accessed via Managed Identities. How do you accept authenticated requests from the external world (outside Azure)?
Since Entra ID (formerly Azure AD) remains the core identity service used by Microsoft, you can configure Azure AD authentication to enable external authentication while keeping your internal security measures intact.
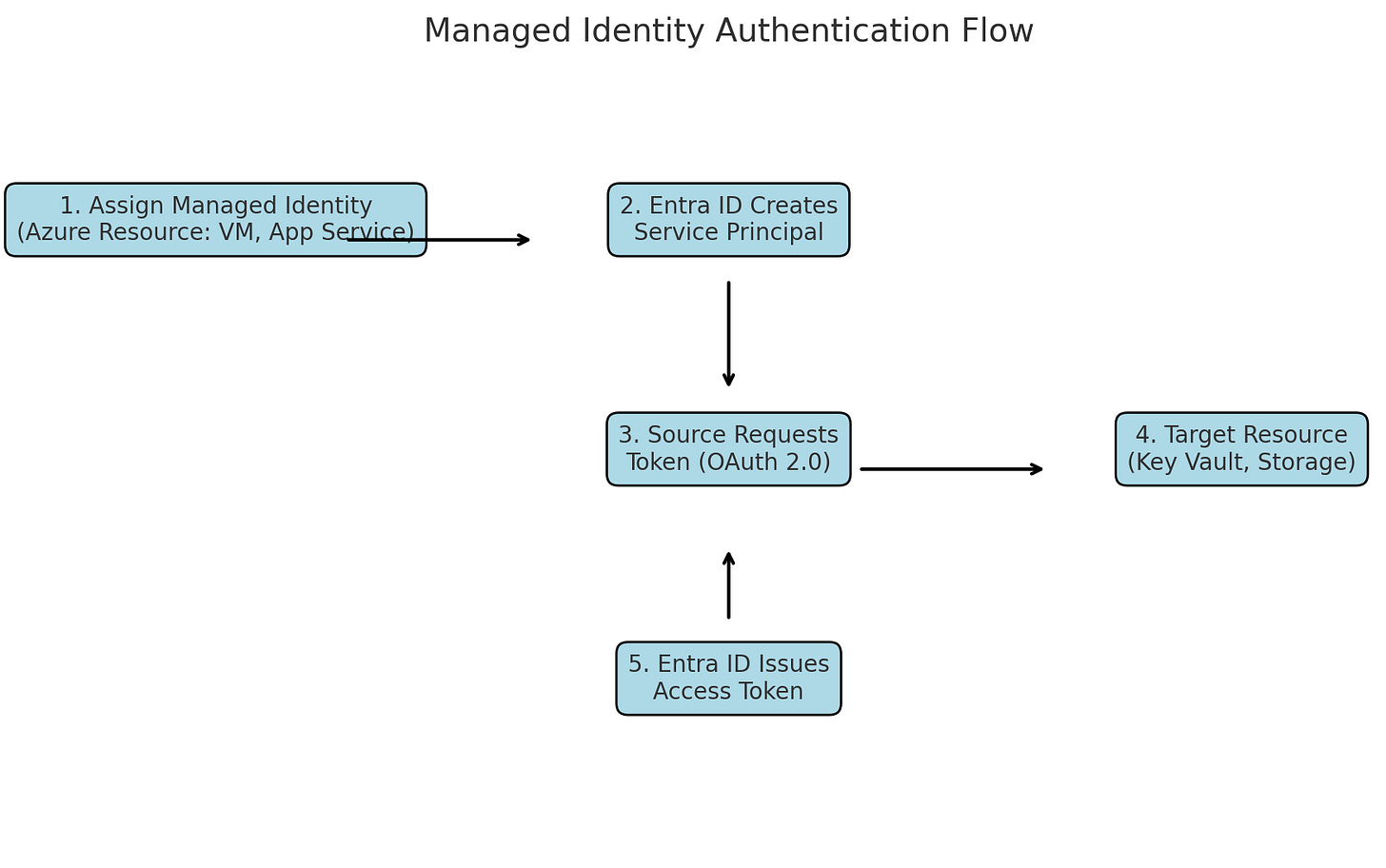
Here is how Managed Identities work:
When you assign a Managed Identity to an Azure resource (e.g., Virtual Machine, App Service), Azure creates a service principal in Entra ID for that resource. This service principal represents the managed identity in Entra ID and is used to authenticate the resource.
The source resource (with its managed identity) communicates with Entra ID to request an OAuth 2.0 token. The request specifies the target resource's identifier (resource URI), like Key Vault or Storage Account.
Entra ID then validates the managed identity’s request. If the managed identity is authorized for the target resource (via role assignments or access policies), Entra ID issues an access token.
Fun fact: The image was generated by AI based on my prompt.
How to make your custom app support Microsoft Entra ID?
Ideally this app will be hosted in Azure App Service:
Go to the Azure Portal and register your app in Azure Active Directory (Entra ID). Note the Application (Client) ID and Tenant ID.
Configure Redirect URI
Set the redirect URI for handling authentication responses (e.g., https://yourapp.com/signin).
Add API Permissions. Specify the required Microsoft Graph or other API permissions. Grant Admin Consent if necessary.
Next step is to:
Enable Azure AD Authentication for Your App Service
Now that your app is registered, you can configure your App Service to require Azure AD authentication for external clients.
Navigate to your App Service:
In the Azure portal, go to App Services, then select your app.
Enable Authentication / Authorization:
In the Authentication / Authorization section of your App Service, turn Authentication to On.
Select Azure Active Directory as the authentication provider.
Configure Azure AD Authentication:
When you select Azure Active Directory, you’ll need to link your app to your Azure AD tenant and set up authentication details.
Choose Express (if you want default settings) or Advanced (if you want more granular control).
Select Azure Active Directory and either:
Use existing AD app: Use the app registration that you created earlier.
Connecting to the custom app:
Using managed identity: Using Managed Identities
From the external world: External clients (users or apps outside Azure) will use OAuth2 authentication to obtain a Bearer token (JWT token) from Azure AD from code.
The external client must include this Bearer token in the Authorization header when making requests to your app.
That’s all for today.